The Proxmox team have released version 8 of the Proxmox Virtual Environment based on Debian 12 (Bookworm). The milestone release also comes with Kernel 6.2 stable as default.
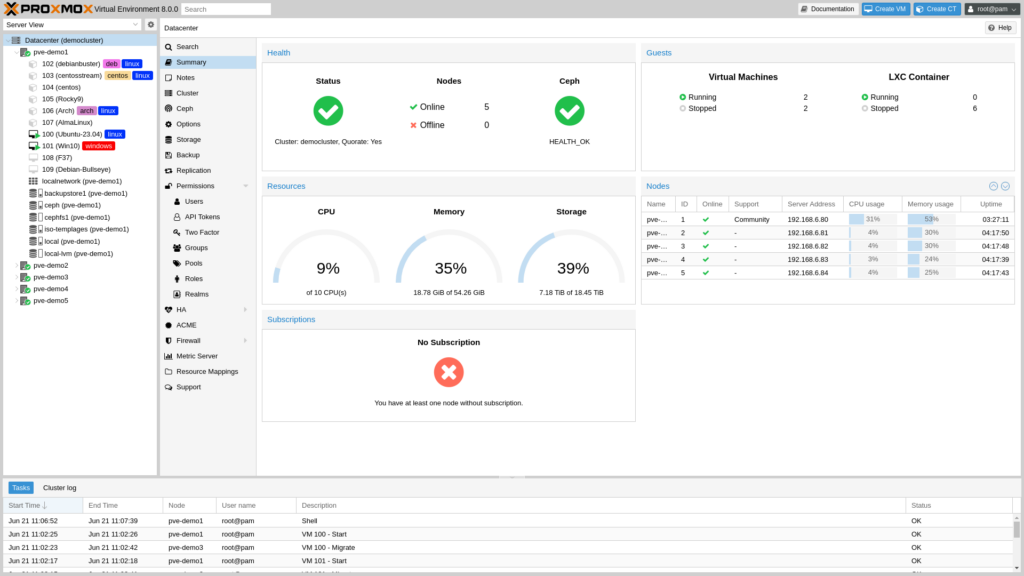
Proxmox VE or PVE is virtualisation software built for enterprise environments. Its is based on KVM (Kernel-based Virtual Machine) which is a well known hypervisor for Linux. PVE combines KVM, Linux Containers (LXC), Ceph, which is software-defined storage (SDS) and networking into one management platform. Best of all, it is free to use with community forums for support. You can of course purchase support if required.
Proxmox includes a web based management GUI (Graphical User Interface) which you can login to after the installation. All management of the virtualisation can be carried out using the GUI, so you dont need to worry about knowing all the command line operations.
With the latest release comes new features, some of which users will be delighted to hear about. So lets take a quick look at some of the features.
Proxmox VE 8 New Features
Proxmox Virtual Environment 8 is based on the latest Debian 12 release and includes support for open source software QEMU 8.0.2, LXC 5.0.2, ZFS 2.1.12, and Ceph Quincy 17.2.6 and of course the newest Kernel 6.2 package.
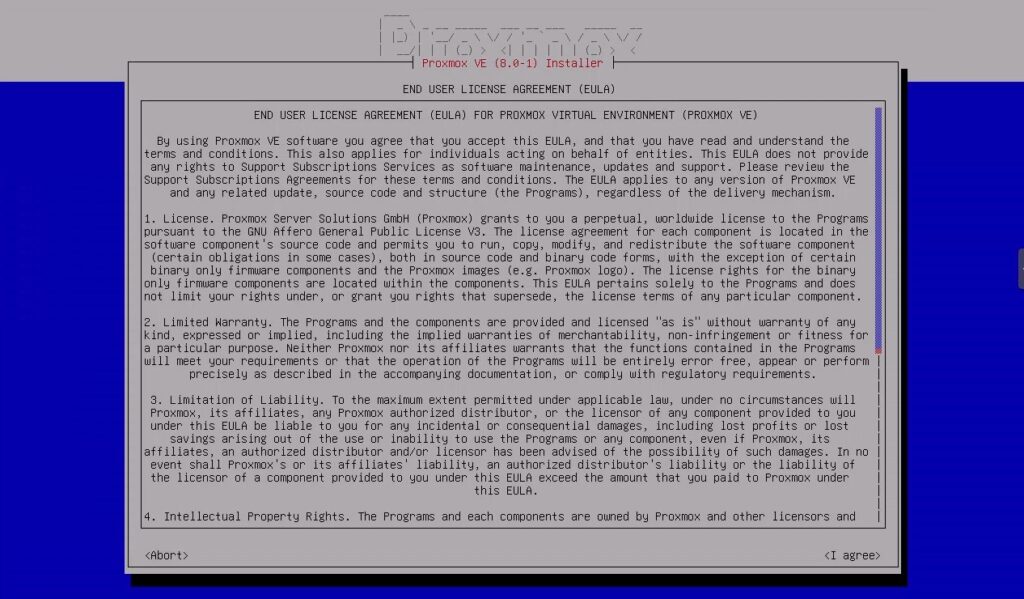
Text-based Installer
Now you can install Proxmox using the new text-based installer. This has been included to help resolve the issues where older (and new) hardware is unable to load the graphical installer.
Repository
The next significant thing in this major release is related to the new Ceph Enterprise repository, which all customers with active Proxmox subscriptions can now access and is recommended for production environments.
When installing Ceph via the web interface or command line, you can now choose between the “Test,” “No-Subscription,” and the new “Enterprise” repository, which is the default.
Resource Mappings
The resource mappings between devices, such as PCI or USB devices and nodes, can now be managed via the API and web interface. The mappings are also represented in Proxmox VE’s ACL system, allowing a user to be granted access to one or more specified devices without the need for root access.
For environments that require virtual machines with hardware passthrough to be able to migrate to other nodes offline, mappings can be used to ensure that the VM also has a valid device for passthrough on the target node.
Proxmox 8 Updated Web Interface
There are several improvements to the web interface. The GUI now includes a dark colour theme which was included in 7.4, however based on user feedback has been refined offering a better user experience. The GUI also checks the subscription status when selecting the Ceph repository and recomments the optimal version for the cluster.
Improved Network Management
One of the highlighted improvements is the network management. The new version of Proxmox allows for synchronisations of users and groups from an LDAP / Active Directory realm. Administrators can manage users with better restrictions which will add more security to the environment. The added integration of VNet and host network bridge access into the ACL also simplifies the permission management.
Virtual Machine Management
There are significant enhancements for VMs. The updated QEMU to version 8 brings support for NetBSD and OpenBSD and a new implementation for the virtiofsd code based on Rust. There are also fixes for various issues such as SMBIOS UUID for Nvidia vGPU passthrough, improved code for volume size information gathering for passed through disks during backup preparation and better align privilege checks in the web UI with the actual privileges required in the backend.
Another improvement is the validation of the provided name when cloning now occurs in the frontend improving & enhancing the user experience. Config files in /etc/pve/mapping and Mapping.* privileges have also been added, preparing for cluster-wide mapping of PCI/USB devices.
Container Improvements
The handling /etc/machine-id on clone operations has had some updates, the file is now only truncated if the source did not set it to ‘uninitialized’ or remove it. The cgroup limit is now set to 99.6% of the configured memory, this allows the container to free up some memory before reaching the Out-of-Memory condition (OOM). The general code has also undergone some improvements which adheres to Perl’s best practices.
Further Proxmox VE 8 Highlights
- New Ceph Enterprise repository: Proxmox Virtual Environment fully integrates Ceph Quincy, allowing to run and manage Ceph storage directly from any of the cluster nodes and to easily setup and manage a hyper-converged infrastructure. The Ceph source code is packaged by the Proxmox development team and—after extensive tests—delivered in the stable Enterprise repository. This unifies the delivery of Ceph with other components of Proxmox VE. With version 8.0, all Proxmox customers with an active subscription can now access the stable Ceph Enterprise repository recommended for production environments.
- Authentication realm sync jobs: The synchronization of users and groups for LDAP-based realms (LDAP & Microsoft Active Directory), can now be configured to run automatically at regular intervals. This simplifies management, and removes a source for configuration errors and omissions compared to synchronizing the realm manually.
- Network resources defined for Software-defined Networking (SDN) are now also available as objects in the access control subsystem (ACL) of Proxmox VE. It is possible to grant fine-grained permissions for host network bridges and VNets to specific users and groups.
- Resource mappings: Mappings between resources, such as PCI(e) or USB devices, and nodes in a Proxmox VE cluster, can now be created and managed in the API and the web interface. VM guests can get such an abstract resource assigned, which can be matched with concrete resources on each node. This enables offline migrations for VMs with passed-through devices. The mappings are also represented in the ACL system of Proxmox VE, allowing a user to be granted access to one or more specific devices, without requiring root access. In case a conflicting entry is detected, e.g. due to address changes or overlaps, users are informed on VM start.
- Secure lockout for Two-factor authentication/TOTP: To further improve security, user accounts with too many login attempts – failing the second factor authentication – are locked out. This protects against attacks where the user password is obtained and a brute-force guess is attempted on the second factor. If TFA fails too many times in a row, the user account is locked out for one hour. If TOTP failed too many times in a row, TOTP is disabled for the user account. The user account can be unlocked again with a recovery key, or manually by an administrator.
- Text-based user interface (TUI) for the installer ISO: A text-based user interface has been added and can now be used optionally to gather all required information. This eliminates issues when launching the GTK-based graphical installer that sometimes occur on very new as well as rather old hardware.
- The x86-64-v2-AES model is the new default CPU type for VMs created via the web interface. It provides important extra features over the qemu64/kvm64, and improves performance of many computing operations.
Download
To get the latest release of Proxmox, Seamless upgrade instructions from Proxmox VE 7.x to 8.x are documented at https://pve.proxmox.com/wiki/Upgrade_from_7_to_8
For a new installation, you can download the ISO from the Proxmox website. Image the ISO to a bootable USB stick using Rufus
Change Log
There is also a large number of changes and bug fixes included, to see the full list you can check the Proxmox change log.
As always you can get support direct from Proxmox or by visting the Proxmox forum.




