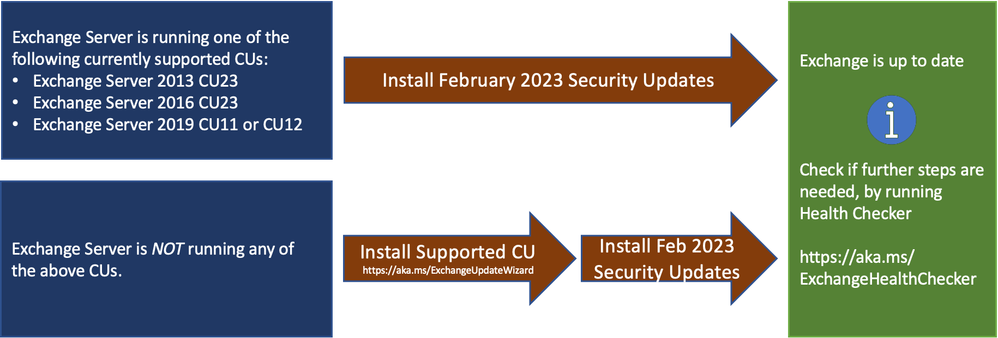
Microsoft has released Security Updates (SUs) for vulnerabilities found in:
- Exchange Server 2013
- Exchange Server 2016
- Exchange Server 2019
SUs are available in a self-extracting auto-elevating .exe package, as well as the original update packages (.msp files), which can be downloaded from the Microsoft Update Catalog.
SUs are available for the following specific versions of Exchange Server:
- Exchange Server 2013 CU23 (note that support and availability of SUs end on April 11, 2023)
- Exchange Server 2016 CU23
- Exchange Server 2019 CU11 and CU12
The February 2023 SUs address vulnerabilities responsibly reported to Microsoft by security partners and found through Microsoft’s internal processes. Although we are not aware of any active exploits in the wild, our recommendation is to immediately install these updates to protect your environment.
These vulnerabilities affect Exchange Server. Exchange Online customers are already protected from the vulnerabilities addressed in these SUs and do not need to take any action other than updating Exchange servers in their environment.
More details about specific CVEs can be found in the Security Update Guide (filter on Exchange Server under Product Family).
Update installation
The following update paths are available:
- Install the latest CU. Use the Exchange Update Wizard to choose your current CU and your target CU to get directions.
- Inventory your Exchange Servers to determine which updates are needed using the Exchange Server Health Checker script. Running this script will tell you if any of your Exchange Servers are behind on updates (CUs, SUs, or manual actions).
- Re-run the Health Checker after you install an SU to see if any further actions are needed.
- If you encounter errors during or after installation of Exchange Server, run the SetupAssist script. If something does not work properly after updates, see Repair failed installations of Exchange Cumulative and Security updates.
Known issues with this release
- Exchange Toolbox and Queue Viewer fails after Certificate Signing of PowerShell Serialization Payload is enabled (Note: this is an issue with the Certificate Signing of PowerShell Serialization Payload feature, not an issue with the security update)
Issues resolved in this release
- Version error when you install Exchange Server in RecoverServer mode – going forward, February 2023 and newer SUs will not cause this issue (but modifications made by the January 2023 SU might still require manual action during a server recovery operation, so the steps outlined in the article might still apply with later SUs installed)
- After the January 2023 SU is installed on Exchange 2016 or Exchange 2019, web page previews for URLs shared in OWA do not render properly
- Some Exchange services do not start automatically after installing January 2023 Security Update
- PowerShell Serialization Payload Signing can now be enabled if Exchange Server 2013 is in the organization
FAQs
Our organization is in Hybrid mode with Exchange Online. Do we need to do anything?
Exchange Online is already protected, but this SU needs to be installed on your Exchange servers, even if they are used only for management purposes. If you change the auth certificate after installing the February 2023 SU, you should re-run the Hybrid Configuration Wizard.
The last SU we installed is a few months old. Do we need to install all SUs in order, to install the latest one?
SUs are cumulative. If you are running a CU supported by the SU, you do not need to install all SUs in sequential order; simply install the latest SU. Please see this update FAQ blog post for more information.
Do we need to install SUs on all Exchange Servers within our organization? What about ‘Management Tools only’ machines?
Our recommendation is to install Security Updates on all Exchange Servers as well as servers or workstations running Exchange Management Tools only, which will ensure that there is no incompatibility between management tools clients and servers.
This post might receive future updates; they will be listed here (if available).
The Exchange Server Team
Read full article (Microsoft Exchange Blog)
All content and images belong to their respected owners, this article is curated for informational purposes only.